Hacking
There are various methods to reverse engineer apps. Usually, you have to decompile the app, bypass SSL pinning, and then you can start looking at the code and requests it makes. However, this app didn't seem to have any SSL pinning. I was able to view the requests the app made by just visiting the desktop site and then using developer tools to switch to mobile view. Don't allow this if you're an app developer.
Now that I could see the requests, I started to use the app and see what requests were made. I tried creating accounts, logging in to my own account, or playing around with my profile. It was time to see if I could find a vulnerability.
I started by recreating some of the browser's requests in Node JS. I happened to copy the change bio request and it seemed to work locally. The request looked something like...
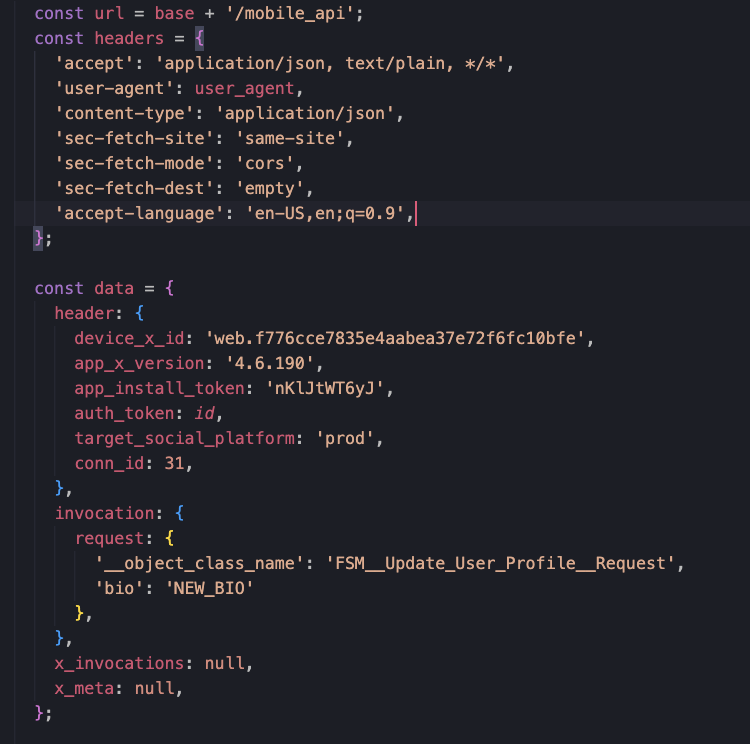
So after recerating the request, I started to play around with some of the fields I was passing in. I first wanted to see if an obvious XSS vulnerability existed. Thankfully, to my knowledge, there wasn't one. I did notice that the auth_token field seemed to be related to my public user id. To confirm, I tried loading other profiles and noticed I could easily get their auth_token as well.
What if I could use this auth_token to make requests on behalf of other users? Well, I tried it and it worked. This was a generic case of IDOR (Insecure direct object references). I was really suprised that an app that my friends and I used had such a vulnerability.
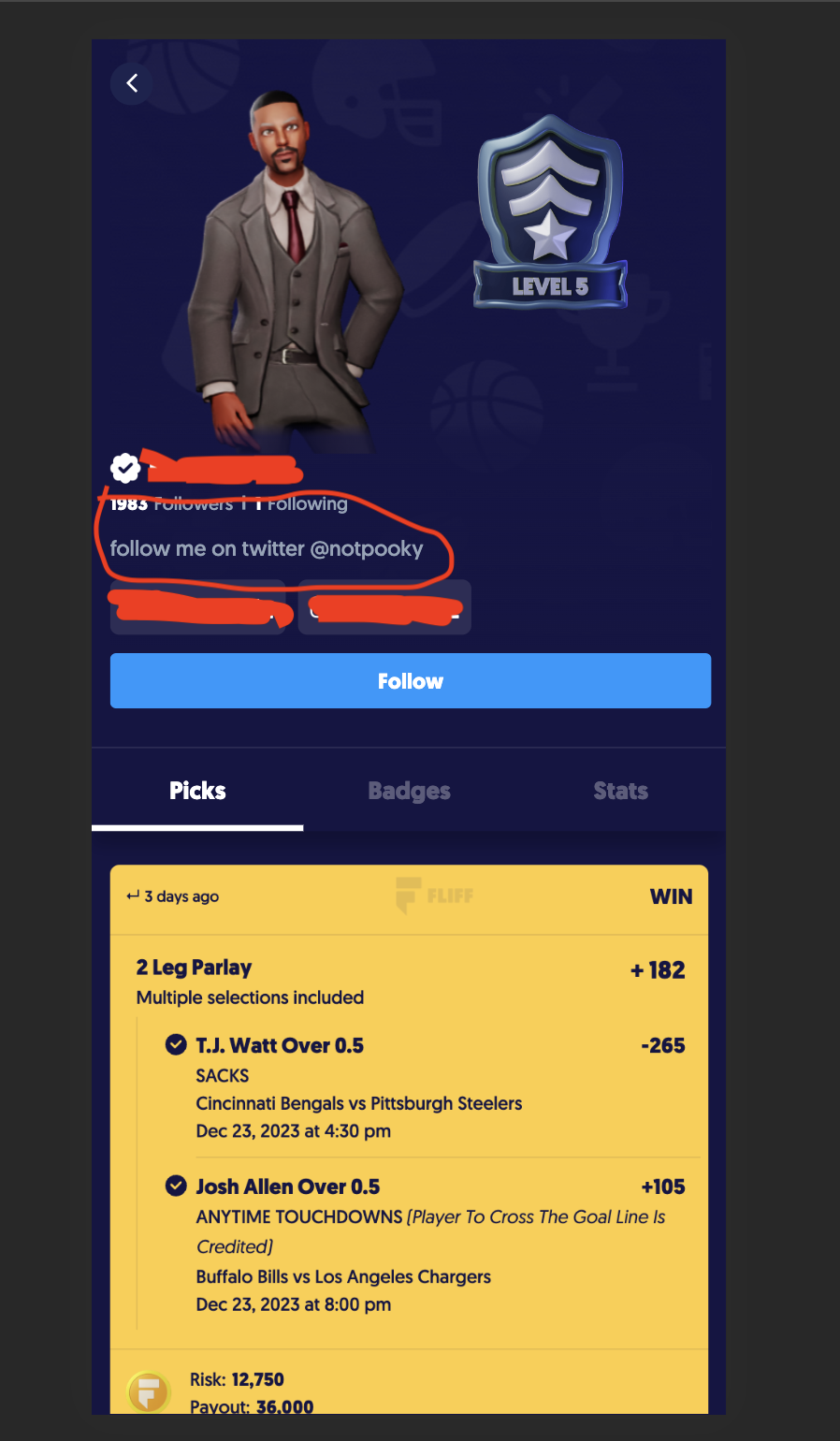
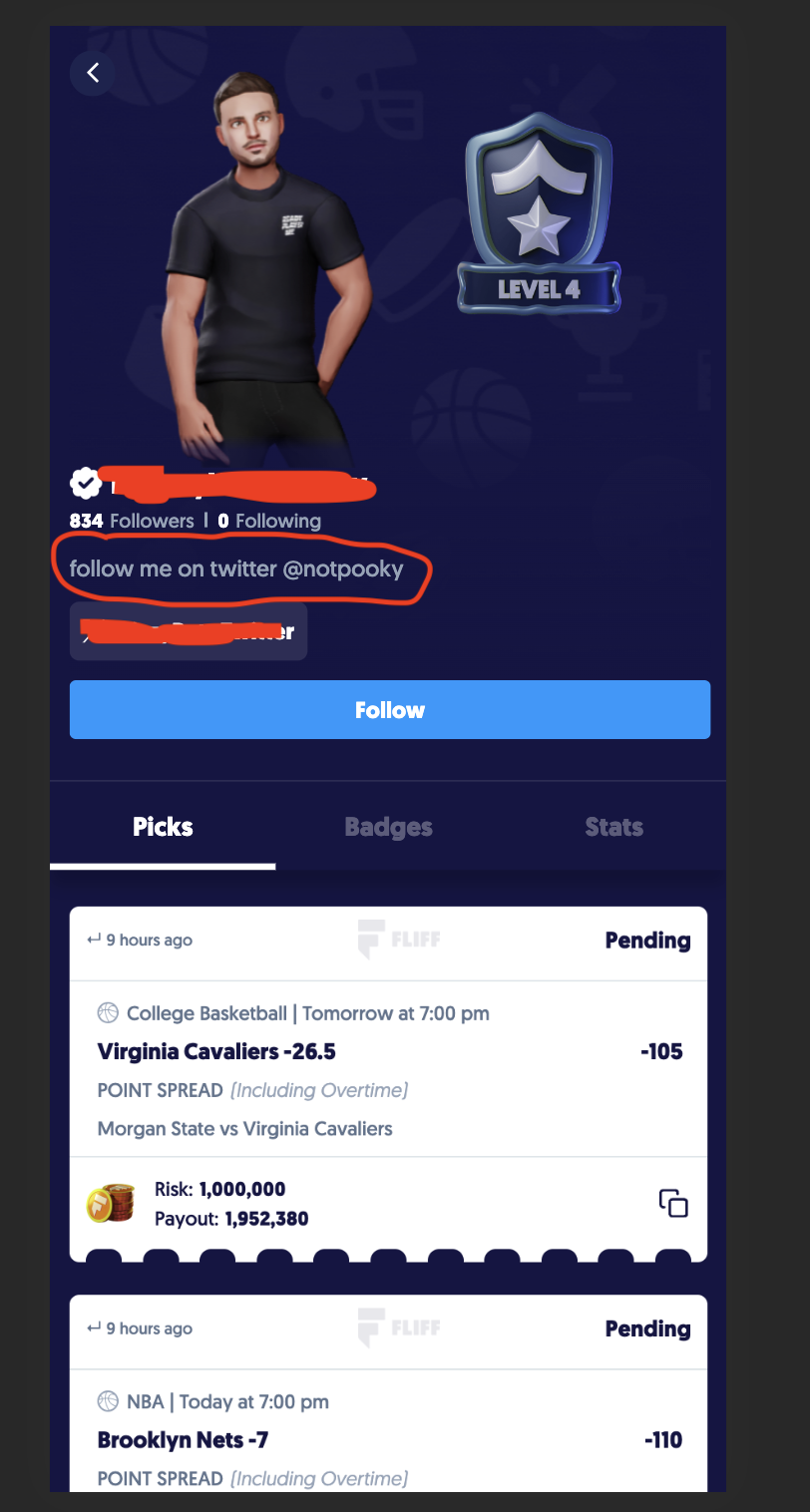
I tried to find other IDOR vulnerable endpoints, but changing bios was the only one I could find. I looked for ways to report the bug directly to the company, but I couldn't find any. So, I just changed some of the top profiles' bios to say "follow me on twitter".