HTTP Requests
To communicate with their backend, websites use HTTP requests. If you open devtools on a store like Nike, you can see the thousands of requests the website makes to their servers to load images, information about sneakers, etc.
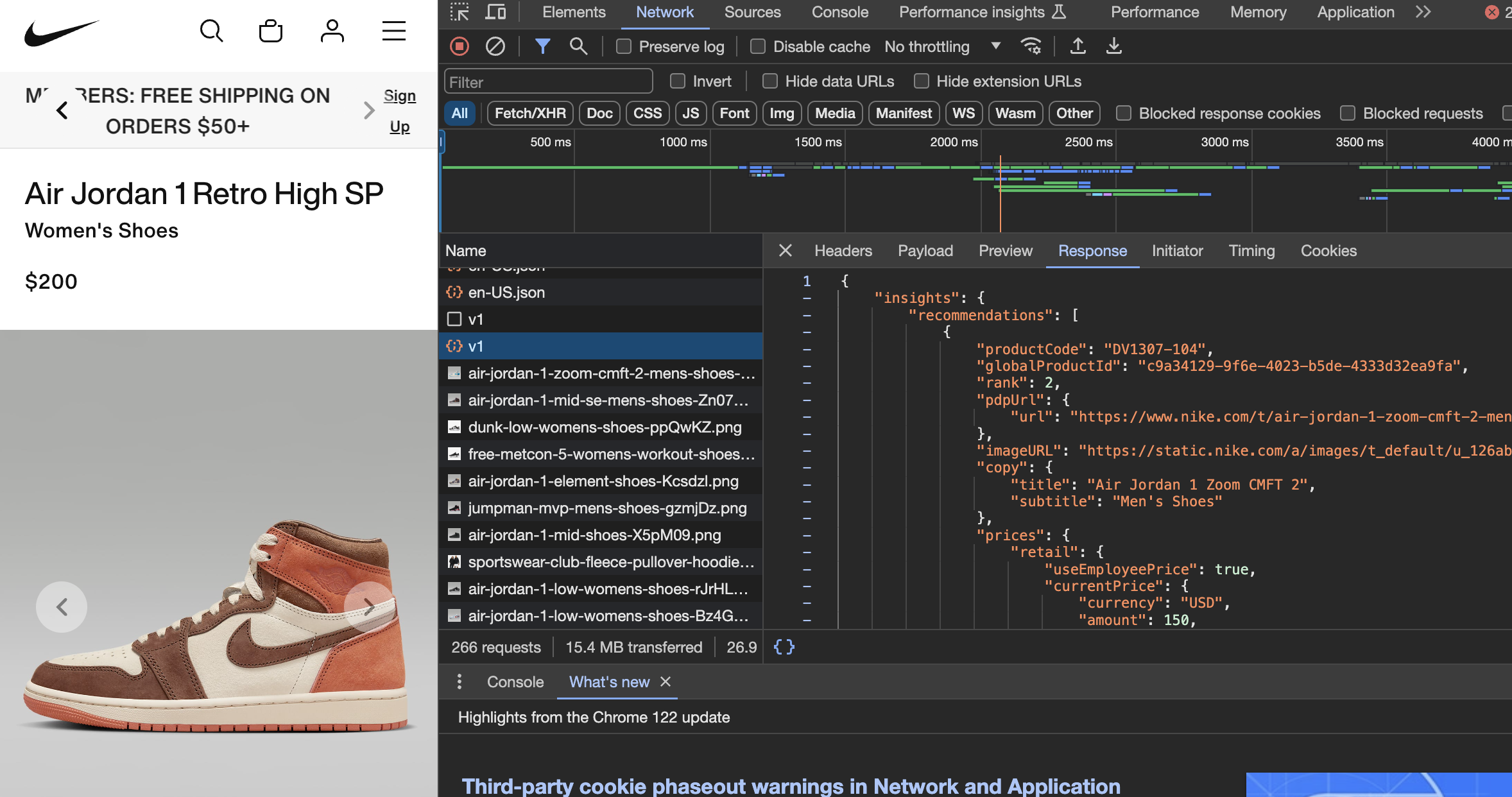
Bots use these same requests to automate the checkout process. They send requests to the store's server to add items to their cart and eventually checkout. For example, if a bot wants to add to cart sneakers on Nike, it replicates the same request that Nike's website makes when you click the "Add to Cart" button.

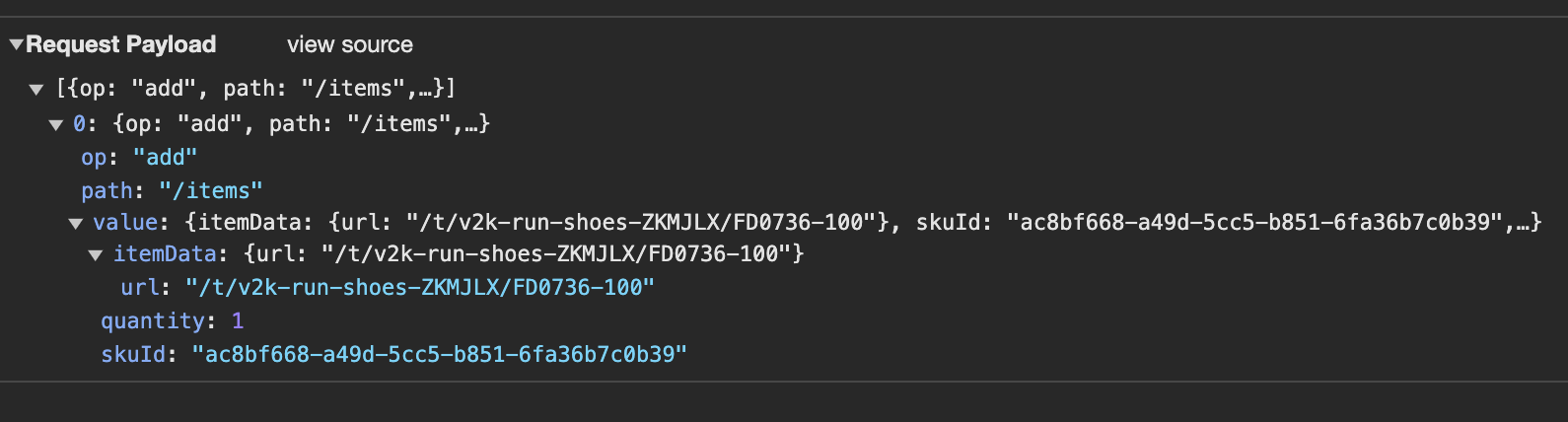
You may be wondering how you can actually do this with code. Certain languages like Python and Javascript have libraries called request clients that allow you to send HTTP requests. Popular ones include Axios for Javascript and Requests for Python.
Seems simple enough. Just find what requests you want to make, write code using a request library, and you made your first bot. Unfortunately, it's not that easy. 99% of the time, websites don't want people botting their products and have measures in place to attempt to stop them. Websites, like Nike, use antibots to detect bots making malicious requests and block them. They also serve to stop cases of fraud, DDoS attacks, and other malicious activity. However, despite the efforts of these sites, bots are often able to bypass these measures.